
This mini tutorial will show off Radare2’s forensic analysis
potential.
You can use radare2 as a digital forensic analysis tool on disks, files,
websites, remote storage.. Etc
Radare2 has a great potential to become the swiss army knife of CTF
contests.
Sure, there are many tools out there that can do what we want. But one
tool do do it all? I don’t think so.
I had created this CTF style image a while ago for a Windows 7 mini
forensic contest.
JPG files are great. You can hide data in plain sight. You can embed archives or other files. You can even change bit sequences to add your data and encrypt it as if it’s part of the image without being detected!
So, vikings have stolen my precious flag. I mean, look at them, so badass in their original file (which you need to follow along).
WARNING. I do NOT own the rights to the image. The original image is meant to be used for EDUCATIONAL purposes only. All rights reserved Leolas Fargue
I heard they looted multiple villages and hidden it within matroushka
chests. (How did the Russian maffia get involved in this?!?)
Luckily for us, there are no keys or passwords for those chests.
Before we open to analyze our JPG let’s look at the Exif data, Exif data is rich in information.
exif vikings_stole_my_flag.jpg EXIF tags in 'vikings_stole_my_flag.jpg' ('Motorola' byte order):--------------------+----------------------------------------------------------Tag |Value--------------------+----------------------------------------------------------Image Description |R29vZCBKb2IhICBGTEctRXhJZl9pc19GdW4gCg==X-Resolution |72Y-Resolution |72Resolution Unit |InchDate and Time |2017:05:06 22:37:47YCbCr Positioning |CenteredExif Version |Exif Version 2.1Components Configura|Y Cb Cr -FlashPixVersion |FlashPix Version 1.0Color Space |Internal error (unknown value 65535)Pixel X Dimension |0Pixel Y Dimension |0--------------------+----------------------------------------------------------
The image description looks interesting seems like base64.
Analyzing it in the Linux commandline with functions is simple:
echo R29vZCBKb2IhICBGTEctRXhJZl9pc19GdW4gCg== | base64 -dBut I prefer to try out radare2’s builtin rahash2 binary for the job
rahash2 -D base64 -s R29vZCBKb2IhICBGTEctRXhJZl9pc19GdW4gCg==Let’s open and analyze our vikings image and analyze it.. I think we’re not done
r2 vikings_stole_my_flag.jpgaaaaafl
Nothing interesting here
We could go to the visual mode V(V) and start searching for bits that
resembled specific signatures but that’s too hardcore.
Searching the docs I found an easier way.Let’s identify the libmagic
data using the pm command:
pm0x00000000 0x00000000 1 JPEG image , EXIF standard0x00000000 1 JPEG image , EXIF standard
Tadaaa! We now know it’s a JPEG image (Thank you captain Obvious!)
No really, we can search more info with pm. There are multiple commands
to use.. for example searching for specific strings and bits of data in
files and directories.
pm?|Usage: pm [file|directory]| r_magic will use given file/dir as reference| output of those magic can contain expressions like:| foo@0x40 # use 'foo' magic file on address 0x40| @0x40 # use current magic file on address 0x40| \\n # append newline| e dir.magic # defaults to /usr/share/radare2/2.2.0/magic| /m # search for magic signatures
Now le’ts search for magic signatures in the file. Depending on the file size this can take a while.. But no problem if it finds something usefull.
/m-- 0 b16060x00000000 0x00000000 2 JPEG image , EXIF standard0x0000000c 0x0000000c 2 TIFF image data, big-endian0x000b1510 0x000b1510 2 7-zip archive data, version 0.30x00000000 2 JPEG image , EXIF standard0x0000000c 2 TIFF image data, big-endian0x000b1510 2 7-zip archive data, version 0.3
Tadam, there seems to be a hidden 7-zip archive hidden at 0x000b1510
s 0x000b1510
px
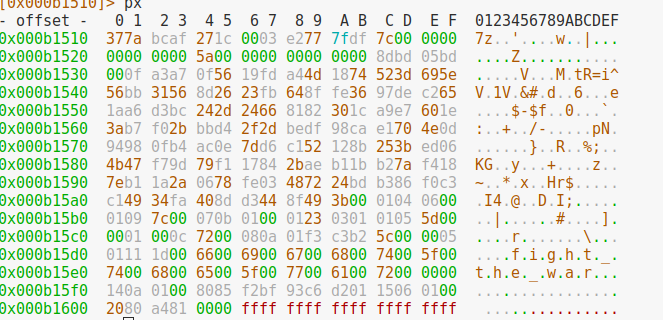
So from 0x000b1510 to 0x00b160C we have data
Let’s see if we can write that to a file, we know that w? is a write function let’s review what it can do for us.
Great, we have a WTF - write to file function, let’s see what it can do
wtf?|Usage: wt[a] file [size] Write 'size' bytes in current block to 'file'| wta [filename] append to 'filename'| wtf [filename] [size] write to file (see also 'wxf' and 'wf?')| wtf! [filename] write to file from current address to eof
So the wtf! can write to file from the current address to EOF (end of file). Since we have already seeked to the location of the 7z we can simply output a file
wtf! archive.7zqq
Listing the file shows us that there is a file fight_the_war, let’s extract it.
7z l archive.7z 7z e archive.7z
ls -lah fight_the_war-rw-r--r-- 1 lostone lostone 114 May 6 2017 fight_the_war
If we where to try and read the data we would only have gibberish… is it encrypted? Or is it another file format? We can always find out
We can analyze it with r2 and file to confirm our findings.
r2 -c 'pm' -q fight_the_war0x00000000 0x00000000 1 gzip compressed data, has original file name{file-name:the_last_battle}: "the_last_battle", from Unix, last modified Sat May 6 21:08:23 20170x00000000 1 gzip compressed data, has original file name{file-name:the_last_battle}: "the_last_battle", from Unix, last modified Sat May 6 21:08:23 2017file fight_the_warfight_the_war: gzip compressed data, was "the_last_battle", last modified: Sat May 6 18:08:23 2017, from UnixInteresting, a file in a file. Some kind of Inception or mathrouska is
happening here.
Good for us we know that it was named the_last_battle and it’s gzipped
gzip -d fight_the_wargzip: fight_the_war: unknown suffix -- ignored
Seems we have to rename it
mv fight_the_war the_last_battle.gzgzip -d the_last_battle.gz
Now we have another file, let’s try to identify it again.
r2 -c 'pm' -q the_last_battle0x00000000 0x00000000 1 xz compressed data0x00000000 1 xz compressed dataSo we have an xz compressed file. Note that we need to rename it with the correct suffix again for this to work.
mv the_last_battle the_last_battle.xzxz -d the_last_battle.xzr2 -c 'pm' -q the_last_battlefile the_last_battlethe_last_battle: ASCII textNow let us feast upon our flag:cat the_last_battleFLG-HideInPlainSightConclusion
In this tutorial I’ve showed how radare2 can be used for forensic analysis. But radare2 is more than that, it’s a full featured Reverse engineering framework.
I hope you enjoyed this mini tutorial, leave a comment or contact me if this has been informative!
